
Criminals get the information they use to breach your company in what is called the social engineering attack cycle. But you don’t have to be an expert on the social engineering framework to protect your business. A good managed service provider will train your team on how to prevent phishing attacks and other cyber security risks.
>>Avoid falling for phishing attacks with our free cheatsheet.
The Social Engineering Attack Cycle: 4 Simple Steps
- Information gathering: Cyber criminals spend a lot of time and resources on gathering information because the better the information, the easier the following steps will be. They might use a phishing technique, or simply try to “friend” you on social media (looking at the photos you’ve posted, scrutinizing them and finding a little something that tells them enough about you to give them a way in).
- Establishing rapport and relationship: Once they’ve gathered enough information, the next step is to try to build some sort of relationship with you. This can happen on social media, by email, phone call, text or other method. That initial contact may seem innocent, but it’s a step to something more.
- Exploitation: They’re in. They have some sort of relationship with you. Now it’s time to hook you. They might send you what looks like a legitimate link about something you have an interest in, or trick you into giving them your email or password. This step requires you to take some action and is a great opportunity for training to make a big difference.
- Execution: Bingo! You’ve been hacked and you don’t even know it. In fact, you may even think you’ve done something good for someone else. By the time you realize you’ve been scammed, the criminal has done the damage, cleaned up his footprints and made sure he leaves no trace behind.
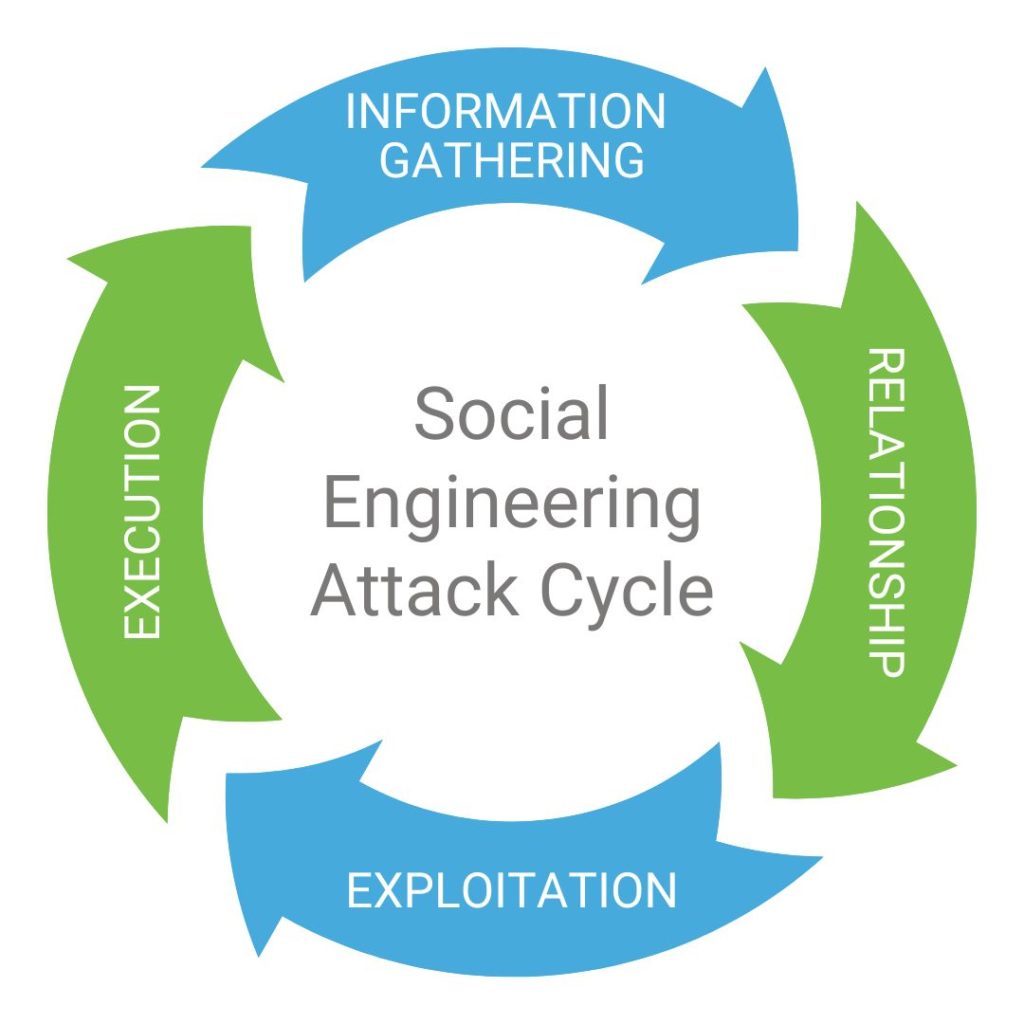
The Social Engineering Framework in Action
You had such a great time at that restaurant and the food was so good, you decide to post a photo on Facebook, Twitter or some other social media platform.
But be careful. Those types of photos are catnip to hackers. Believe it or not, cybercriminals can get a lot of information from them and even trick you into contacting them and thereby finding out everything about you and your contacts.
One of the ways is to pretend they’re the manager of that restaurant, gym, movie theater etc. You’re thanked for your patronage and offered discounts for the next time you come in. Don’t click on those links or respond. It’s just a phishing expedition that will lead to trouble.
Photos taken at your business are also rife with information. Hackers can zoom in on your badges, or on the computer screen in the background, even on a post-it note which is in the frame.
Protect Your Cyber Security on Social Media
Thanks to social media, there is already a ton of information out there about people to leverage. Make yourself a harder target with these tips:
- Take a look at what you share, especially photos, and make sure there are no hints about you–even ones that seem insignificant.
- Trust no one who suddenly appears and encourages you to accept a freebie. Remember nothing is really ever free.
- Never lend your “expertise” about something to others on social media. Even if they are legit, if you personally know them, still be wary but perhaps find another way of sharing.
If your social media account is hacked:
- Check all your financial accounts. This is where criminals can do the most damage, so start here. If you see any suspicious behavior, report it and lock down the accounts. Notify your banks and credit agencies. Change your login credentials. The new password should be difficult and not one that has been used before on any account. Learn more in our Password Management Guide.
- Change your passwords for all social media sites as well, starting with the one that was compromised.
- Alert your social network about the hack. Your hack could give criminals a way to establish rapport with your friends and compromise their accounts.
- Think about what accounts you may have used your social media account to log in to (that “Login with Facebook” button). Change those account credentials and disable the “login with” feature. Individual passwords are more secure.
Here at Internos, we know all the tricks these hackers and cyber criminals use because we keep up to date with their techniques. So contact us or book a meeting, virtual or in person. There’s no obligation and no sales pitch, just a conversation about the right approach to IT support and cyber security for your business.
Use our Managed Service Provider Checklist to Find the Right
Our easy-to-follow checklist can guide you through the process of the best IT services provider for your business.
Are you a first-timer to IT support? Maybe you aren’t happy with your current MSP? This checklist will help you outline and define:
