
Sounds like some good rhyming words for a poem or song? Maybe, but in terms of data breaching, it’s really some of the ways to steal, compromise and control your data. Keep reading to learn more about protecting your business from phishing, smishing, vishing and whaling.
Phishing
Almost everyone has heard about phishing but some don’t really know what it means. Here’s an example: People receive an email from some company or person they know. The email claims that their data has been compromised and instructs them to click on a link in the email. When they do, they’re hacked. The email looks like it’s legitimate and coming from a reputable company, but it is not. It’s a way to disrupt, destroy or steal your data and unfortunately it works. The cyber criminal quickly gains access to your network where they may steal information, disrupt business or simply lie in wait for the right opportunity to lock it down and demand a ransom. Or, more often than not, all of the above.
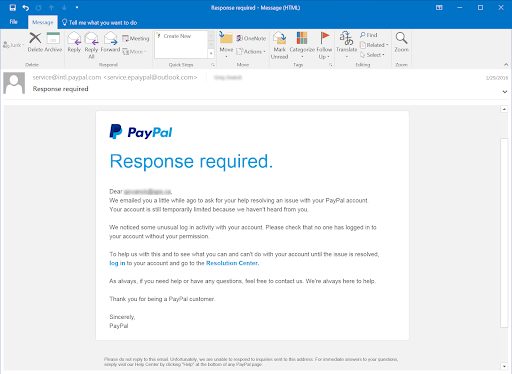
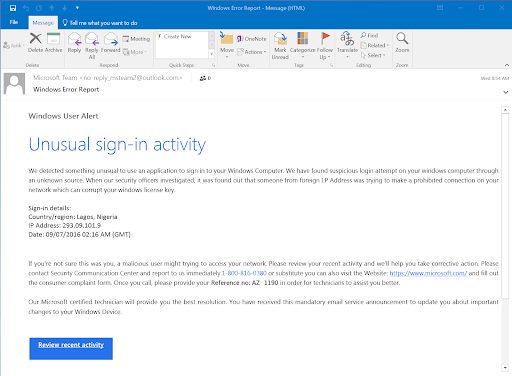
Phishing emails usually convey an urgency for the recipient to act. They use the language and tone of that business and include some sort of personal knowledge that convinces the target to open the email. If they do, the target’s system is infected with malware.
>>Don’t get hooked in a phishing attack. Download the Phishing Prevention Cheat Sheet.
Smishing
This is much the same as phishing, but it comes from a text message. The word smishing comes from “SMS,” meaning text message. Again, the goal is to trick you into clicking on a bogus link in the text message, often driving you to a realistic (but fake) login screen where your username and password can be captured.
Smishing is a bit harder to detect because the text message itself usually does not provide as much information as an email does. It might look like it comes from your bank or some other source you use like PayPal, but again, it’s not. It might even say you’ve won something but the only thing you will receive is trouble.
Doubt everything. Banks, insurance companies, the IRS and vendors will not send you text messages like this. Instead of clicking on the link, simply log in to your account through the normal website or app and check for messages there.
Vishing
Phishing is email, smishing is text and “vishing” is for phone calls (v for voice). In this case the criminal calls or leaves a voicemail. Sometimes it’s one of those “robo calls” that are easier to spot, but it can also be a real person and surprisingly convincing. Like with other tactics, a sense of urgency is used to trick you into acting before thinking. The message might say your credit card is about to be blocked, your insurance is about to expire or other similar scary issues. To prevent those events, the caller asks you to verify information, like your credit card numbers, date of birth, address and more. Then they have all they need to impersonate you to make purchases on your cards or even drain your bank account.
Here’s a hint to avoid this: NEVER give that kind of information to anyone calling you unless it’s someone you personally know. Even then, it’s not a good idea. Instead, call the published customer service line for the company (often on the back of your credit card) the caller claims to represent, ask about your account status and if the problems are real, resolve them.
Whaling
If a “fish” is a general employee of any company, a “whale” is its CEO, president or other senior level position. Upper level people are a rich target for data hackers because those at the top tend to have access to all aspects of a business’s network. Whereas a general employee would only have access to files they need for their work, a CEO will have access to all files, plus banking, HR and other high-value data for hackers.
Whaling is any cyber attack that is directly targeted at one or more senior level employees, whether it’s by phishing, smishing, visthing, pharming or other tactics.
Pharming
In pharming, cyber criminals bypass the need to trick you into going to a fake site to enter your data and instead simply program your computer to send you there. Pharming can be caused by an infected computer (malware based) or a corrupted server (DNS server poisoning). In either event, it redirects your browser from the site you want to visit to a fake version where cyber criminals can capture your data.
Pharming is really tough to recognize as it uses the DNS (domain network system) cache and the user’s device or provider’s network equipment. Cache is a list of the websites and URLs that you have accessed. Flushing out your cache files is a good way to keep your system clean. But this won’t help in the case of a poisoned server.
Be wary of downloading software from the internet as it might have a pharming virus or other harmful object embedded in it. This is where a top-rated security software such as Norton or McAfee can help.
Definitions in a Nutshell
Though similar, phishing, smishing, whaling, vishing and pharming all have the same purpose: to steal, hack or totally destroy your data. They do it by different means:
- Phishing is done by email
- Smishing is done by text
- Vishing is done by a phone call
- Whaling targets high-ranking officials
- Pharming uses the DNS cache or your provider’s network
And those are just a few of the more common ways cyber criminals get a hold of your data, with other tactics emerging daily.
Protect Your Data Cheat Sheet
The absolutely best way to protect your data, both business and personal is training. Train your staff how to recognize the bogus emails, texts and voice messages. Here are some tips to include:
- Don’t be quick to respond. Roll over the sender’s name and any links attached. Make sure the urls match the “from” email. It should be based on what you’d expect on the sender’s address. Make sure it truly comes from the url you use. It should have the full email address you’re accustomed to: For example, look for a from address like joe@yourbankswebsiteaddress, not from joe@gmail.com.
- Set-up a multi-factor authenticator (MFA) such as one from Microsoft, Google or Last Pass.
- Don’t click on downloads from sites like Dropbox or even Google. Go to the site your normal way and see if the download in the email is actually on those sites. Often you can hover over the link, read it and see if it is legit.
- Never put your personal or business email on any website unless the URL starts with https:// The “S” in the https: stands for secure.
- When in doubt, call. From your contact list, call the bank, insurance company or personal contact and find out if they really did send you that email. Chances are they did not.
>>Don’t get hooked in a phishing attack. Download the Phishing Prevention Cheat Sheet.
If you have questions about this article contact us or book a meeting, virtual or in person. We’re happy to help.

