
Keeping up with the latest in cyber security fraud attempts can be a struggle for many businesses out there. You’d think an expert managed service provider like Internos would be immune to cyber attacks; think again!
Recently, our company was threatened by a seemingly innocent request to access our Google My Business account. A malicious actor pretending to be a real person named “Joseph Scott” sent a request to be added as an owner of our Google My Business account.
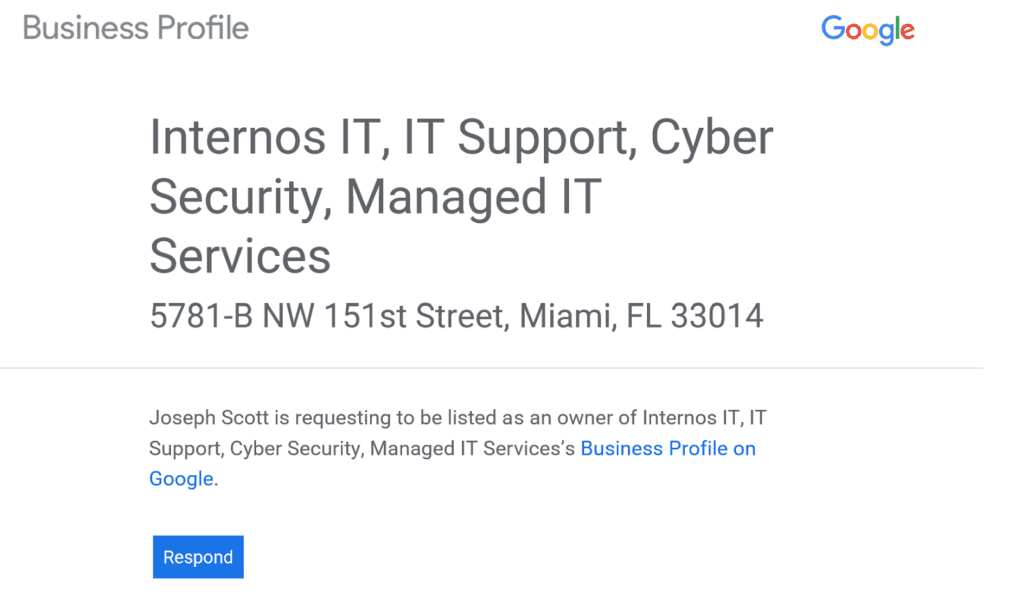
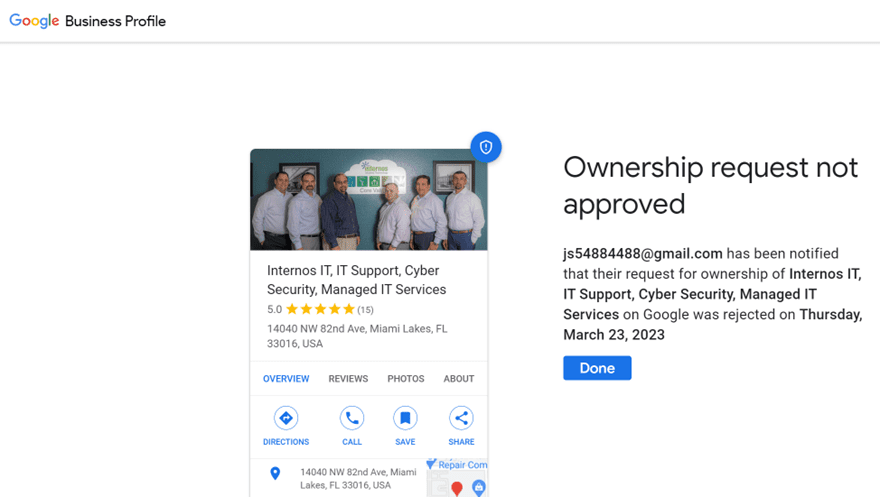
The request originated from outside our organization and led back to a suspicious-looking, seemingly randomly generated email account. Needless to say, we blocked the request.
How to Respond to a Request for Access
Requesting access to sensitive company information through secure accounts isn’t a phishing scam in the traditional sense. Traditionally, the scammer spoofs an email to trick you into clicking the link and giving away personal information. In this case, they are hoping you will willing give them access to your account.
Here are the five best things you can do if this type of scam happens to you:
1. Don’t simply delete the email and hope it solves the problem
You must actively protect your company against cyber criminals that would love to take your Google My Business away from you and sell it to the highest bidder (or even hold it for ransom).
2. Reject the request
The best course of action you can take when you get a request for access to a company account is to select the option to review the request and then reject it.
3. Activate 2-factor verification
As an added precaution, we recommend activating Google’s 2-step verification process for your associated GMB account. This sends a code to your phone before you can access anything on that account.
Multi-factor authentication is critical in today’s cybercrime-infested world. Protect yourself and your account in any way you can. Monitor the inbox linked to your GMB and reject all requests within 3 days.
4. Notify your internal Google My Business team when you get an ownership request
Double-check with your internal company team to make sure the requester isn’t somebody from within your company. Without knowing there is a problem, they have no hope of fixing it.
5. Secure your account with a strong password and use a password manager
If security is a top priority, sign out of all sessions and change your password to a very strong one (a string of random numbers and letters at least 12 characters long is best). Then use a secure password manager to store them.
Keeping Your Business Secure
It’s important to note that as an organization of any size, you should remain constantly vigilant about any potential cyber security breach attempts. Approving a seemingly innocuous request for access to something could be the difference between securing your business and opening the floodgates for ransomware, credential theft, and much worse.
If you have any questions about cyber security or want to hear about the latest in cybercrime prevention, contact us or book a meeting with one of our experts.

